Introduction
I saw the headlines, and I knew the truth. Unfortunately, I wish more people did too.
On June 18th, 2025, Cybernews released an article detailing the discovery of datasets containing roughly 16 billion passwords. This article was most recently updated June 30th, 2025 as of the time of this writing. I am sure everyone reading this is aware of the discovery, and I'm sure many of you have decided for yourselves the course of actions you will take following all of the information you have received.
There have been many examples of ways to protect oneself moving forward, and I advise you to follow them. My purpose in this post is to enlighten those interested in the unjustified spread of misinformation regarding such a massively impactful event.
The Flood
Following the initial headline, a surge of publications regarding the information in the Cybernews article were released which recursively regurgitated information from other sources reporting on the same news. This undoubtedly led to "reliable sources" spreading information they read from somewhere other than the original source.
The dominos continued to fall until one of the largest news magazines in the United States, Time Magazine, released their publication on June 20th with the headline "Billions of Passwords Have Been Leaked in Massive Breach, Researchers Say. Here's What You Should Know".
Three Critical Problems with This Headline
There are three fundamental issues with this headline that exemplify the broader problem:
1. Vague Numbers How many billions? The number has been clear since the beginning: 16 billion. The original article even includes the literal dataset statistics to show it. See the Cybernews article. It should be noted that per the Recent Updates in the article, the screenshots of actual data from the leaks were added after the original release.
2. Misleading Terminology The terms "leaked" and "massive breach" indicate that a single source contained all of the information and that this single source was found at one point in time, very recently. As noted by Cybernews in their original article however, there were 30 datasets collected over the span of the first six months of 2025, and only one of those datasets was publicly disclosed prior to the June 18th publication.
3. False Authority They offer advice on what individuals should know about it and what to do as if they are an authority on the topic. But they only reveal what other sources stated in regards to the origins of the information as well as what Cybernews suggested on changing passwords and making them stronger.
The Cascade Effect
This is just one case study, but per the header of this section, I will simply list a few and definitely not all-encompassing count of the sites that have released similar if not even more misconstrued information on the report:
Mashable reported "Yes, 16 billion passwords leaked online. No, it's not what you think." That article, released on the same day as the Time Magazine publication, is already more clarifying in fewer words than their title, and admittedly hints that many people's immediate assumptions may be wrong.
CBS News reported "16 billion login credentials from Google and other sites leaked online, report says". The targeting of Google is misleading because there is clear reporting that states not any one site was largely compromised out of the 16 billion total records and not even that Google was one of the primary targets. There is however evidence that supports Telegram as a primary source for one of the datasets, albeit one of the smaller collections.
The Fearmongering
Now I've already given reason why this title by Entrepreneur is misleading: "'Largest Data Breach in History': Apple, Google, and Meta Passwords Reportedly Among 16 Billion Stolen in Massive Hack", but there are less explicit motives behind the wording here that feeds the sensationalism certain outlets took advantage of during "The Flood".
Questionable Quoting Practices
Most significantly is the quoting of the words "Largest Data Breach in History". It bothers me that they quoted these words because they never explicitly explain or cite where that quote comes from. Following that quote, the only source actually quoted in the article is Cybernews, the original source. Which would imply that the quoted claim in the title of the article is from the same source, and it is.
But in direct contradiction to the accuracy of the quote, they claim the passwords were stolen from a "Massive Hack" in the same breath. Not only is this a straight up lie, as a single "hack" was not responsible for the disclosure of the datasets. But the choice word of "Hack" when no other news report regarding the event includes that word goes to show an ulterior motive: fearmongering.
Strategic Word Choice
Sure, "breach" and "leak" are in part truthful because of the nature of the data being publicly disclosed, but "Hack" is a targeted word meant to evoke certain emotions. Those emotions certainly include worry, anxiety, or even fear. There is no purpose behind the inclusion of the word other than to hit harder as a headline.
Additionally, TechRadar released a report titled "Over 16 billion records have leaked in 'unimaginable' major data breach - here's what we know". The quotation of "unimaginable" is a secondary example of organizations understanding that a broader audience is being reached, and therefore capitalizing on it.
Prior to the addition of a FAQ on the original post by Cybernews, there was only one mention of the word "unimaginable" on the site, with regards to the record count being 16 billion. Obviously, that is already quite an unfathomable number to many. To TechRadar however, that word means money. One site visitor even commented "the article is just a series of factoids and nothing of substance or any actions".
The Facts
As you may have taken note of yourself, I have yet to actually address the event as a single breach or leak. I hesitate out of consternation of possibly contradicting myself. I am not trying to bash any one source quoted or referenced for being misleading or upholding questionable practices, but I am bringing to light that this is an accepted practice that should be rejected.
It impresses me that so many of the post-day-one publications are still without correction. Even after clarifications have been made by the original source and even third party relations.
The Have I Been Pwned? Clarification
I want to most notably bring up the fact that on June 20th, 2025 at 1:44pm in the afternoon, the creator of Have I Been Pwned? (HIBP) released a statement stating that after a million visitors visited his site in half a day, he needed to clarify none of the data from the found datasets had even been incorporated into the site.
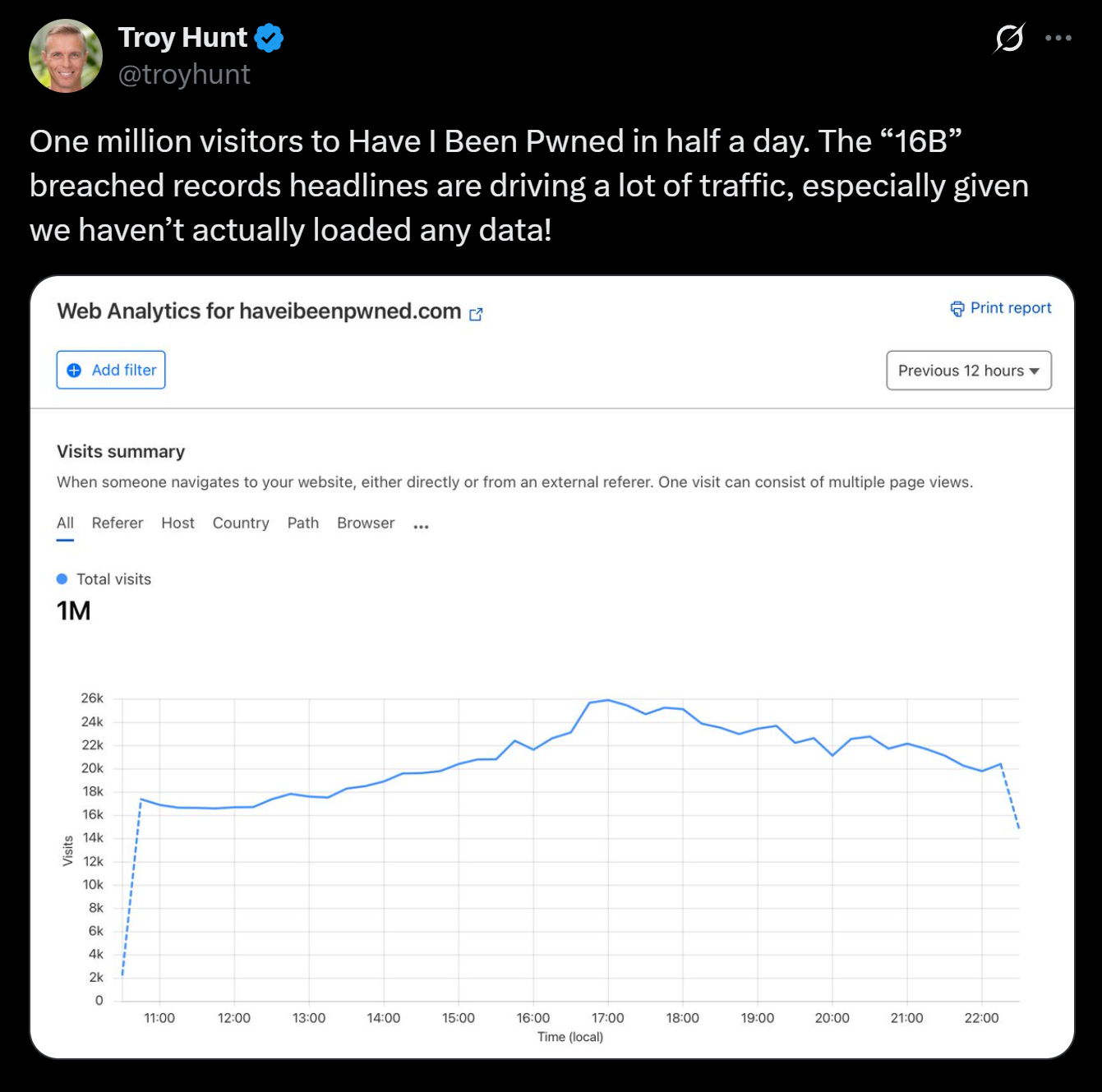
Source: https://x.com/troyhunt/status/1936163179240857663
This is a perfect example of the impact of spreading misinformation and providing a false sense of security for the majority of individuals who quite literally don't know any better.
Persistent Misinformation
Imagine a publication, still unchanged, having been released the same day as this tweet, claiming to go to HIBP to verify if you were a victim. They would be spreading lies. Can you imagine it? Don't believe me?
Well just check the Entrepreneur post I mentioned earlier and scroll to the bottom. And I quote:
"Want to know if your email has been exposed? Check out the website, Have I Been Pwned, which will tell you if you've been affected by a data breach (and how many times)."
Sure, the sentences as they stand are truthful. Have I Been Pwned is notorious for notifying individuals of specific leaks their email(s) can be found in. But if you, a Business News site, are making this statement directly following the context of arguably the "Largest Data Breach in History", how can you not realize your audience will try to validate if they were a part of the data by going to HIBP right then and there? Especially when you're not an authority on the topic!
When Authorities Get It Wrong
Now, the fact of the matter is what about those organizations that are authorities on the topic? Do they understand? Are they careful in the information they are spreading? I would hope so. But they honestly are not, which is why it's so widely acceptable in this modern age for misinformation to spread like wildfire.
My final case study: 1Password. 1Password is a well-regarded password manager, notorious for being one of the few password managers that have seemingly never been the victim of a hack. They can, I presume you would agree, be considered authorities on the topic of a 16 billion password dataset release. They, however, disappointed me.
They made a blog post covering the event on June 20th, 2025. The same day that Troy Hunt of HIBP clearly stated the datasets from the event had yet to be incorporated. As of the time of this writing, without any updates to 1Password's original blog post, the linked site reads:
"For additional reassurance you can enter your email address on Have I Been Pwned to see if it was included in the leak"
That is even more explicit of a lie than Entrepreneur's statement. Claiming that interested persons who are not 1Password customers can still be self-assured by checking HIBP is a falsity I am in disbelief is still being provided as advice by an authority on the topic as of the time of this writing.
Conclusion
The right information is out there. Whether or not the individuals that have been intentionally or unintentionally misled find it is out of my control. But with my final words I want to call for the authorities in the cybersecurity field, or in any field for that matter, to always hold themselves accountable.
Fact-checking should be the job of the provider, not the consumer. Research is performed in the pursuit of truth. So too, should be its release.
In an age where information travels at the speed of light, the responsibility to verify facts before publication has never been more critical. The 16 billion password dataset discovery serves as a stark reminder that even well-intentioned reporting can become a vehicle for misinformation when accuracy is sacrificed for speed and sensationalism. The same social dynamics that fuel misinformation also fuel social engineering attacks, where adversaries exploit trust and urgency to compromise organizations.
As consumers of information, we must demand better. As creators of content, we must do better. The modernization of misinformation isn't just about technology—it's about the choices we make in how we handle the truth. If your organization wants to understand how attackers weaponize misinformation and social pressure, penetration testing that includes a social engineering component is a good place to start.